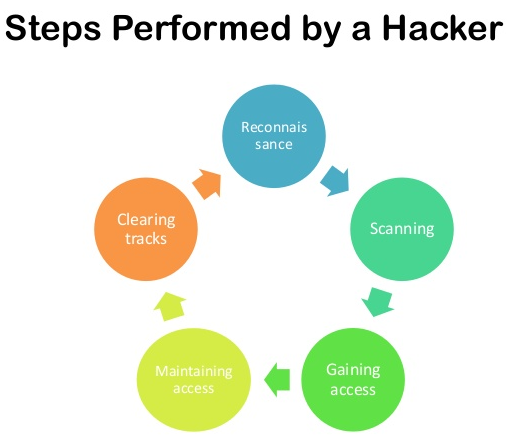
- Performing Reconnaissance
Gather Information about target’s system like operating systems, applications, ports, and services, to successfully exploit them.
Recon can be broken into two categories passive and active.
- Passive reconnaissance - Gathering information about the target without actually "touching"(making connection to) the target, or in a way that looks like normal traffic.
Tools Used:
- Netcraft - To gather info about websites like web server, operating system, last reboot, and other technologies
- FOCA - To gather metadata from documents on a website.
It also include DNS and SNMP mining, dumpster diving, social engineering, using social media such as Facebook and LinkedIn, and Google hacking, among other techniques.
- Active reconnaissance - Gather information about the target by actually sending packets to the target and evaluating the response. The results of active recon are much more specific and reliable, but also much riskier. Anytime we send a packet to a site, our IP address is left behind.
We can use tools like nmap,hping3 to gather information about remote targets like open ports, running services, and operating systems.
It also include network enumeration,banner grabbing and the use of vulnerability assessment tools such as Nexpose, Nikto, and Retina.
- Gaining Access (Exploitation)
Be creative and think about all of the protocols that the system or network uses and how they might be abused. Tools like Metasploit,sqlmap,BeEF,SET are used.
After recon try looking into the vulnerability databases such as SecurityFocus, TechNet,exploit-DB and others for known vulnerabilities and exploits.
Always consider the possibility of a man-in-the middle attack and social engineering attack.
Physical access to a network provide unlimited options while Remote access options are limited but they can be much more malicious.
Note: As soon as Metasploit develops new exploits, the AV companies immediately begin developing new signatures for them.
-
Privilege Escalation
When we get access to the system or network through client-side attacks (attack’s on ordinary user’s vulnerable apps like browser,adobe flash etc) but we will only get privileges of an ordinary user.
We need root or sysadmin privileges to get unfettered access to the entire network. Hence we need to escalate privileges (possible with legitimate account).
After compromising one system on the network we can compromise other systems through it using system privileges.
To get system privileges social engineering techniques can be used like asking for the password under the proper context. -
Leaving Behind a Backdoor or Listener
It is necessary to leave behind a listener or rootkit. It will be there even after system reboot and we can come back to the system to exploit it.
This listener can be in the form of Netcat, a command shell, VNC, Meterpreter, etc. -
Extracting Data
This can be credit card data, personally identifiable information (PII), intellectual property, or other valuable information.
Recub and Cryptcat are two tools that can remove data stealthily. -
Covering Your Tracks
To make certain that our exploits don't lead back to us, we need to cover our tracks. This can take many forms such as clearing log files, removing any software we uploaded, removing our command history, etc.